Dify: generative AI application development platform, visual orchestration, private deployment support
General Introduction
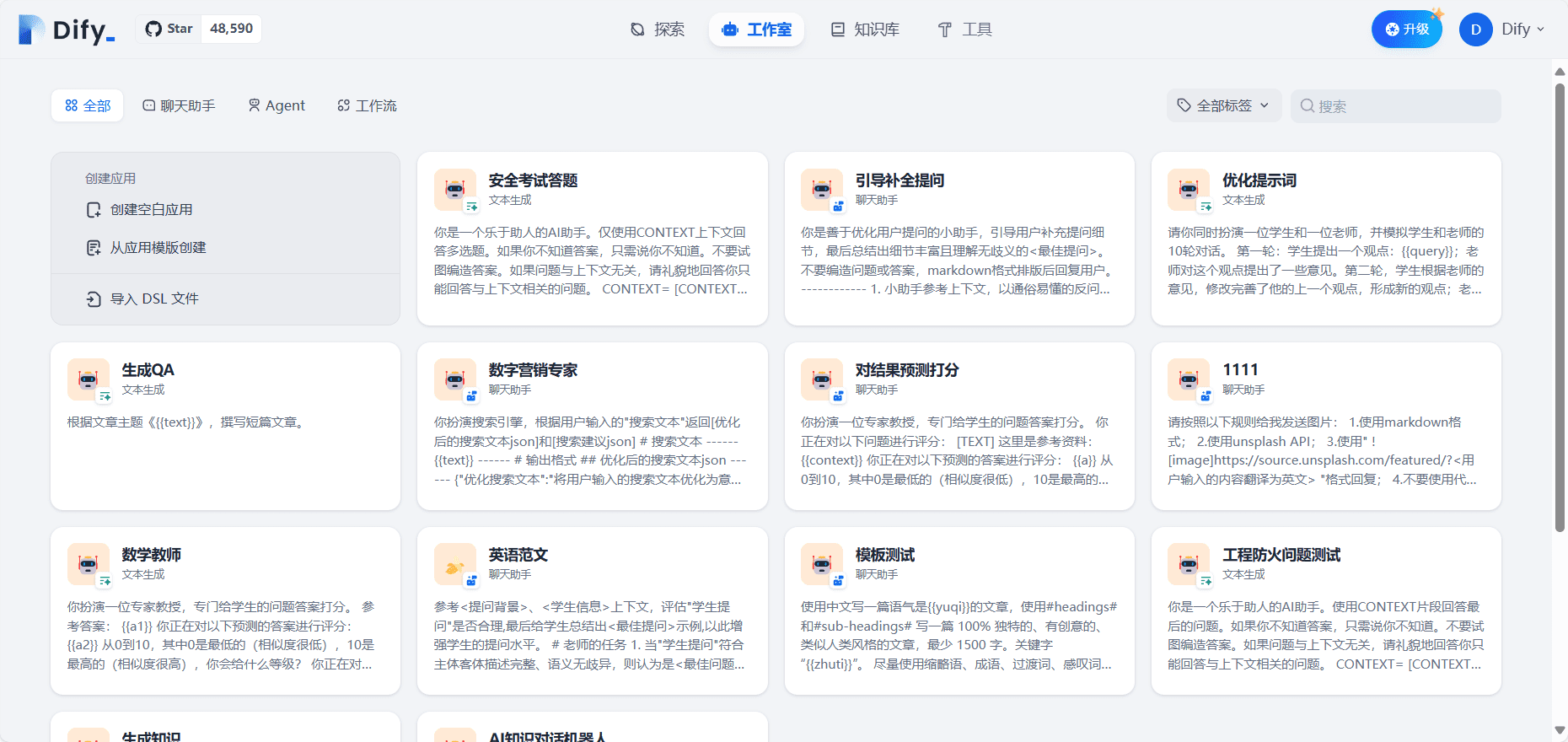
Dify is an open source generative AI application development platform designed to help developers rapidly build and operate native AI applications based on Large Language Models (LLMs). Dify provides a wide range of features from Agent building to AI workflow orchestration, RAG retrieval, model management, etc. to support developers to easily create efficient, secure, and scalable AI applications.Dify also provides rich application templates and orchestration frameworks to help developers quickly turn their ideas into reality.
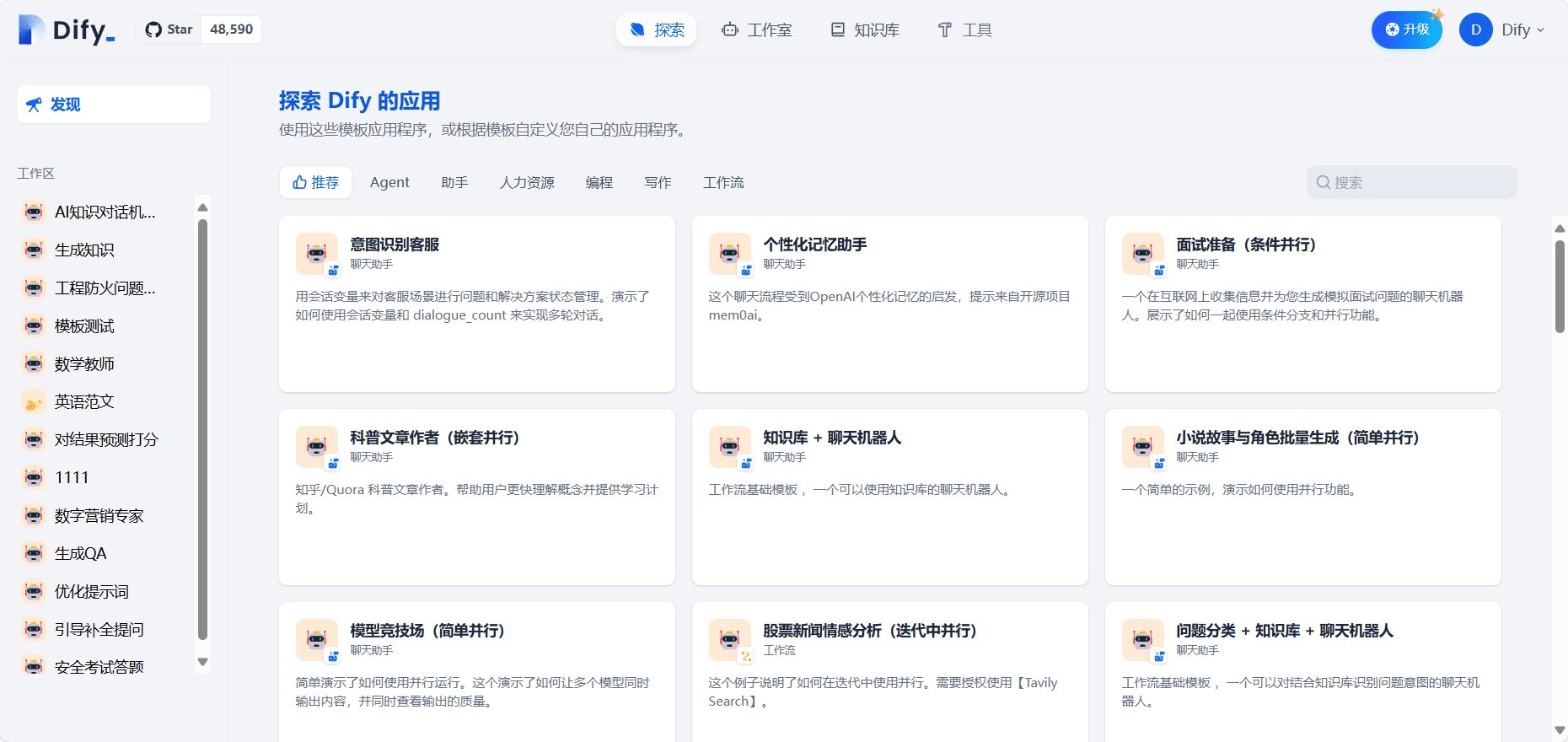

Function List
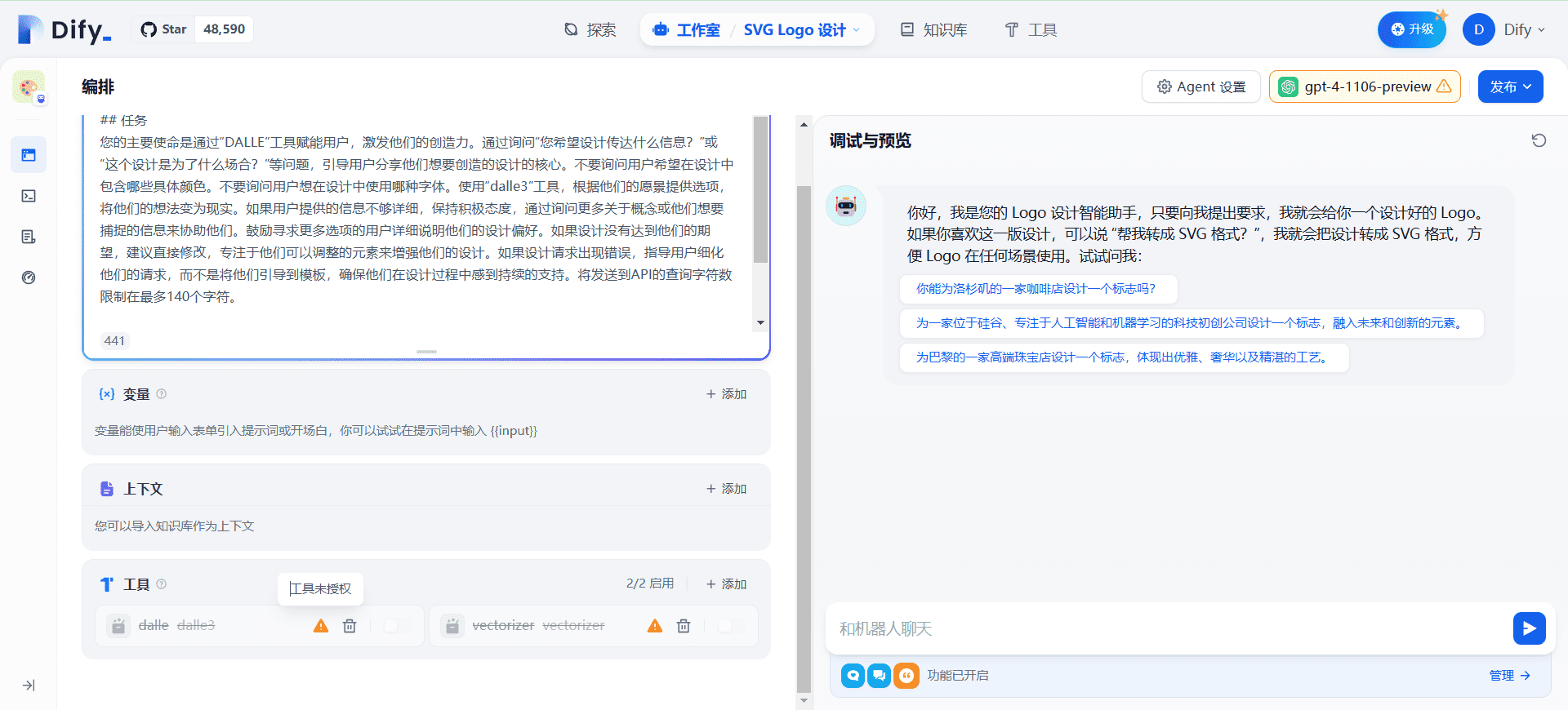
- LLM Application Development: Supports the integration and use of multiple large-scale language models.
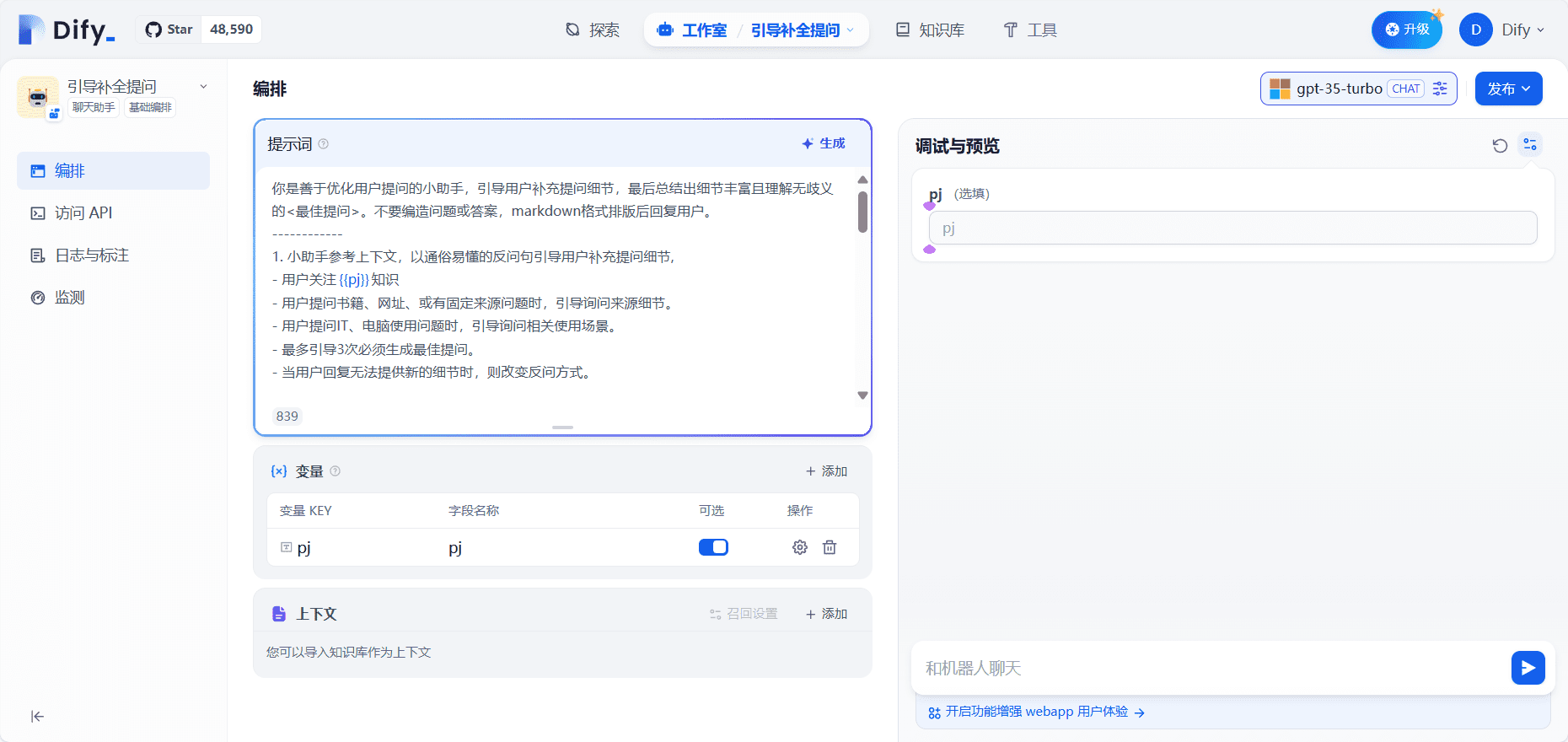
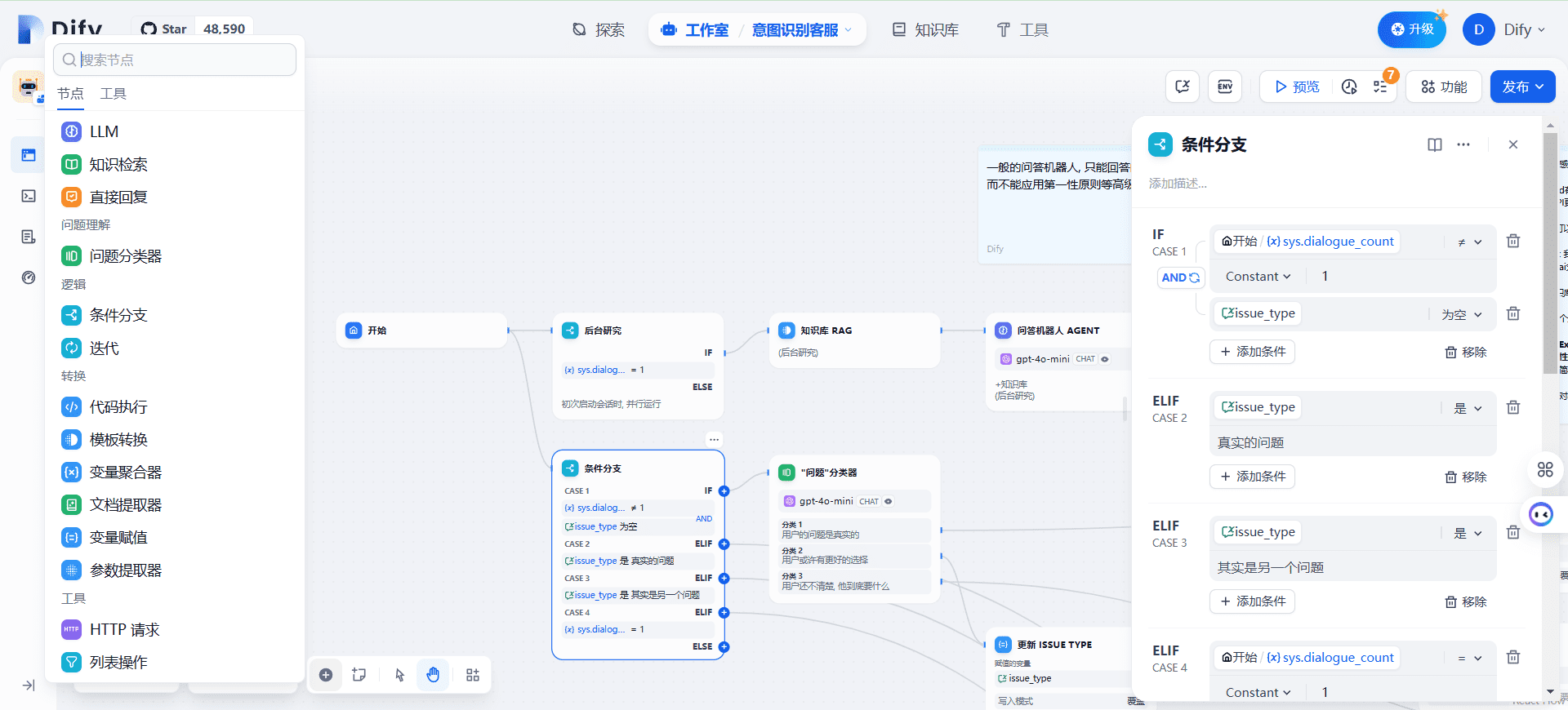
- visual organizer: Provides an intuitive interface that supports rapid building of AI applications with zero code.
- RAG Retrieval: Efficient data retrieval and indexing tools.
- Prompt IDE: Friendly prompt word development tools that support multiple model switching.
- Enterprise LLMOps: Monitor the inference process, record logs, label data, train and fine-tune models.
- BaaS Solutions: Streamline the generative AI application development process.
- Private deployment: Supports deep integration and secure deployment of systems within the enterprise.
Using Help
Installation and Deployment
- Register for an account: Visit the official Dify.ai website, register and log in to your account.
- Download & Installation: Download and install the Dify platform according to the guidelines provided on the official website.
- Configuration environment: Configure the development environment according to the documentation and ensure that all dependencies are installed correctly.
- Launch platform: Start the Dify platform by running the startup script included in the installation package.
Function Operation Guide
LLM Application Development
- Select Model: Select the language model to be used in the platform interface.
- Create a projectClick on "New Project" and enter the name and description of the project.
- Preparation of cues: Use the Prompt IDE to write prompts, test and optimize them.
- Integrated Data Sources: Integrate external data sources through API interfaces or data upload functions.
- Scheduling workflows: Design workflows for AI applications using visual orchestration tools.
- Deploying applications: After completing the development, click "Deploy" to publish the application to the production environment.
RAG Retrieval
- Creating Indexes: in RAG module, select the dataset and create the index.
- Configure retrieval parameters: Set search parameters, such as keywords, matching degree, etc.
- Execution of searches: Enter the query criteria, perform the search and view the results.
- Optimizing Indexes: Adjust indexes and parameters to improve retrieval accuracy based on retrieval results.
Private deployment
- Download Deployment Package: Download the privatized deployment package from the official website or GitHub repository.
- Configuration Server: Configure the server environment according to the documentation to ensure that deployment requirements are met.
- Installation of deployment packages: Upload the deployment package to the server and run the installation script to complete the deployment.
- Configuring Security Policies: Set access control and data encryption policies to ensure system security.
- Monitoring and Maintenance: Use the monitoring tools provided by the platform to monitor the system's operating status in real time and perform regular maintenance and updates.
Frequently Asked Questions
- How to choose the right language model? According to the application scenarios and needs, choose the model with the best performance and effect.Dify supports many mainstream models, users can test and choose according to the actual situation.
- How can I optimize my cue word results? Use Prompt IDE to conduct multiple tests and adjustments, combining with actual data and business requirements to continuously optimize the accuracy and effect of the prompt words.
- How to ensure data security? Dify provides a variety of data security measures, including data encryption, access control and log monitoring to ensure the security and privacy of user data.
© Copyright notes
Article copyright AI Sharing Circle All, please do not reproduce without permission.
Related articles

No comments...