Shadowfetch: Cloudflare Workers Anonymous Proxy Large Model API
General Introduction
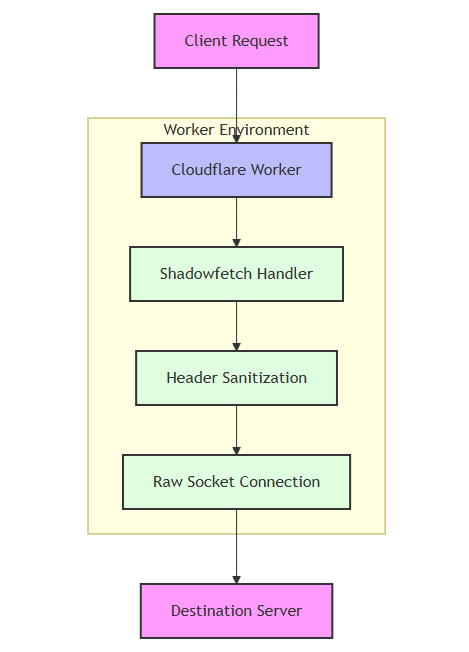
Shadowfetch is a lightweight open source tool for Cloudflare Workers, maintained by developer tysak on GitHub and released under the AGPL v3 license. It replaces Cloudflare Workers' default fetch functionality with native TCP socket request forwarding, and is designed to provide users with a higher level of privacy protection. In contrast to the built-in fetch, which leaks sensitive information such as user IP, geolocation, etc., Shadowfetch ensures that only the necessary data is passed during a request by removing unnecessary metadata and headers. It is suitable for developers or applications with high privacy requirements, such as proxy services that require anonymized requests.
The reason that using Cloudflare Workers to invert all kinds of big-factory APIs can lead to blocking is that Cloudflare Workers can compromise your privacy, and this solution is mainly used to securely vigorously all kinds of big-model APIs.
Function List
- Privacy Protection Request Forwarding: Remove sensitive headers (such as user IP and geolocation) that Cloudflare adds by default.
- Native TCP Socket Support: Bypass the built-in fetch metadata injection by using a direct TCP connection.
- Lightweight design: Reduce resource consumption and ensure fast response, suitable for high-frequency request scenarios.
- configurableSupport for user-defined target URLs and authentication tokens for flexible adaptation to different needs.
- Open Source Collaboration: Based on the AGPL v3 license, community contributions of code and optimization suggestions are welcome.
Using Help
Shadowfetch is a tool that runs in the Cloudflare Workers environment and requires some technical background to install and use. Below is a detailed installation and operation guide to help users quickly deploy and get started.
Installation process
Shadowfetch requires source code via GitHub and deployment in Cloudflare Workers. Here are the steps:
1. Preparing the environment
- pre-conditions::
- You have registered for a Cloudflare account and enabled the Workers feature.
- Install Node.js and npm (for the Wrangler tool).
- Install the Wrangler CLI tool for Cloudflare:
npm install -g wrangler - Log in to Wrangler:
wrangler login
2. Get Shadowfetch source code
- Clone or download the Shadowfetch repository:
git clone https://github.com/tysak/shadowfetch.git cd shadowfetch
- 如果项目没有提供独立的 `wrangler.toml` 文件,需手动创建:
```toml
name = "shadowfetch-worker"
type = "javascript"
account_id = "你的 Cloudflare Account ID"
workers_dev = true
3. Configuration code
- Open the main script file in the project (usually the
index.js), modify the configuration as required. For example:const CONFIG = { AUTH_TOKEN: "your-auth-token", // 用于验证请求的令牌 DEFAULT_DST_URL: "https://example.com", // 默认目标地址 DEBUG_MODE: false, // 调试模式开关 }; - Save the file when the configuration is complete.
4. Deployment to Cloudflare Workers
- Run the following command in the project directory to deploy:
wrangler publish - After a successful deployment, Cloudflare returns a Workers URL (such as the
https://shadowfetch.your-account.workers.devThe service can be accessed via this URL.
5. Validation of deployment
- utilization
curlor browser testing services:curl https://shadowfetch.your-account.workers.dev/image/https://example.com - If a response is returned to the target server that does not contain sensitive headers (such as the
cf-ipcountry), indicating a successful deployment.
How to use
The core functionality of Shadowfetch is to intercept requests through Workers and forward them in a privacy-preserving manner. Here are the details of the operation:
Basic request forwarding
- trigger method: Shadowfetch is based on the path pattern (e.g.
/image/https/...) to intercept the request. For example:curl https://shadowfetch.your-account.workers.dev/image/https://example.com - processing flow::
- Workers receive the request.
- Shadowfetch removes all sensitive headers (such as the
cf-connecting-ip). - Direct connection to the target server via TCP socket (
https://example.com). - Returns the response from the target server.
Configuring Customized Targets
- Setting in the code
DEFAULT_DST_URL, all unspecified destination requests are forwarded to this address. For example:const CONFIG = { DEFAULT_DST_URL: "https://api.example.com" }; - Redeployment:
wrangler publish
Add Certification
- If you need to restrict access, you can set the
AUTH_TOKEN. Client requests are required to carry the token in the headers:curl -H "Authorization: your-auth-token" https://shadowfetch.your-account.workers.dev/image/https://example.com - Requests that do not carry the correct token will be rejected.
Featured Function Operation
Privacy
- View Results: Compare the request headers using Shadowfetch and the default fetch:
- Default fetch:
cf-ipcountry: CN cf-connecting-ip: 1.2.3.4 - Shadowfetch:
(仅保留必要头信息,如 Content-Type)
- Default fetch:
- Operating Methods: No additional configuration is required and it takes effect automatically after deployment.
debug mode
- start using
DEBUG_MODEView detailed logs:const CONFIG = { DEBUG_MODE: true }; - After deployment, access the Workers log:
wrangler tail - The logs show request processing details, making it easy to troubleshoot problems.
Recommendations for use
- test environment: Local use is recommended for initial deployment
wrangler devTesting:wrangler dev - Update Code: Periodically pulls the latest version from GitHub:
git pull origin main wrangler publish - Community Support: Submit feedback on GitHub Issues or contribute to the code if you encounter problems.
usage example
1. HTTP proxy
You just need to append the destination URL to the address of your deployed worker in the following format:
https://你的_Cloudflare_Worker_域名/密码/https://目标网站/其他路径
An example:
https://bequiet.pages.dev/fonts/https://destination.example.com/dns_query
Visiting that link forwards the request to the https://destination.example.com/dns_queryand no longer expose their real IP!
2. WebSocket proxy
To proxy a WebSocket, simply replace the target protocol with one that begins with wss://.
The format remains:
wss://你的_Cloudflare_Worker_域名/密码/wss://目标网站/其他路径
Example:
wss://bequiet.pages.dev/fonts/wss://destination.example.com/chatroom
One click to transit to wss://destination.example.com/chatroomThe
Frequently Asked Questions
- Why is shadowFetch better for privacy?
Because it won't carry Cloudflare's own assortment ofcf-This means that your request is a "clean native TCP connection" in the eyes of the target server. This means that your request is a "clean native TCP connection" in the eyes of the target server. - How do I turn on debugging to view logs?
classifier for objects with a handleDEBUG_MODEenvironment variable is set totrueThat's it. You'll be able to see detailed request and response debugging information in the worker log. - Can I not use the default AUTH_TOKEN for the password?
You can change it to your favorite string in the environment variable, such as "mySecret", and then the link will have to follow with the same "mySecret" in order to successfully proxy.
© Copyright notes
Article copyright AI Sharing Circle All, please do not reproduce without permission.
Related posts

No comments...