Open source tool for detecting security risks in MCP services
General Introduction
mcp-is-dangerous is an open source tool developed by Shaojie Jiang on GitHub. It helps users detect security risks in the use of MCP (Model Context Protocol) services for AI tools through simple Python code. The tool shows potential threats where external tools may access environment variables or files, and aims to alert users to security issues. It is compatible with the author's extendable-agents Project related, highlighting the ease of tool sharing alongside the risks. Projects are for education and testing only and do not support malicious use.
Function List
- sensing MCP Whether the service can be exploited for malicious purposes.
- Providing Tool Functions
get_environment_variables, showing access to environment variables. - Reveal the security vulnerability of MCP services with code samples.
- Support for connecting custom MCP clients to test service security.
- Remind users to run in an isolated environment to verify risk.
Using Help
How to install and run
This tool requires a basic Python environment. Here are the detailed steps:
- Checking the Python Environment
Make sure Python 3.8 or later is installed. Type in the terminal:
python --version
If you don't have it installed, you can download it from the Python website.
- Download Tools
Run the following command in the terminal to clone locally:
git clone https://github.com/ShaojieJiang/mcp-is-dangerous.git
Then go to the catalog:
cd mcp-is-dangerous
- Installation of dependencies
needfastmcplibrary to run the MCP service. Installation method:
pip install fastmcp
For security purposes, a virtual environment is available:
python -m venv venv
source venv/bin/activate # Windows 用 venv\Scripts\activate
then run pip install fastmcpThe
- starter kit
Run it in the catalog:
python main.py
When the terminal displays "Server running...", the tool is started. When the terminal displays "Server running...", the tool is started.
- test function
Detect with command line:
uvx mcp-is-dangerous
Example output:
Here are what I could find:
PATH /usr/***
HOME /home/***
Main function operation flow
- Detecting environment variable access
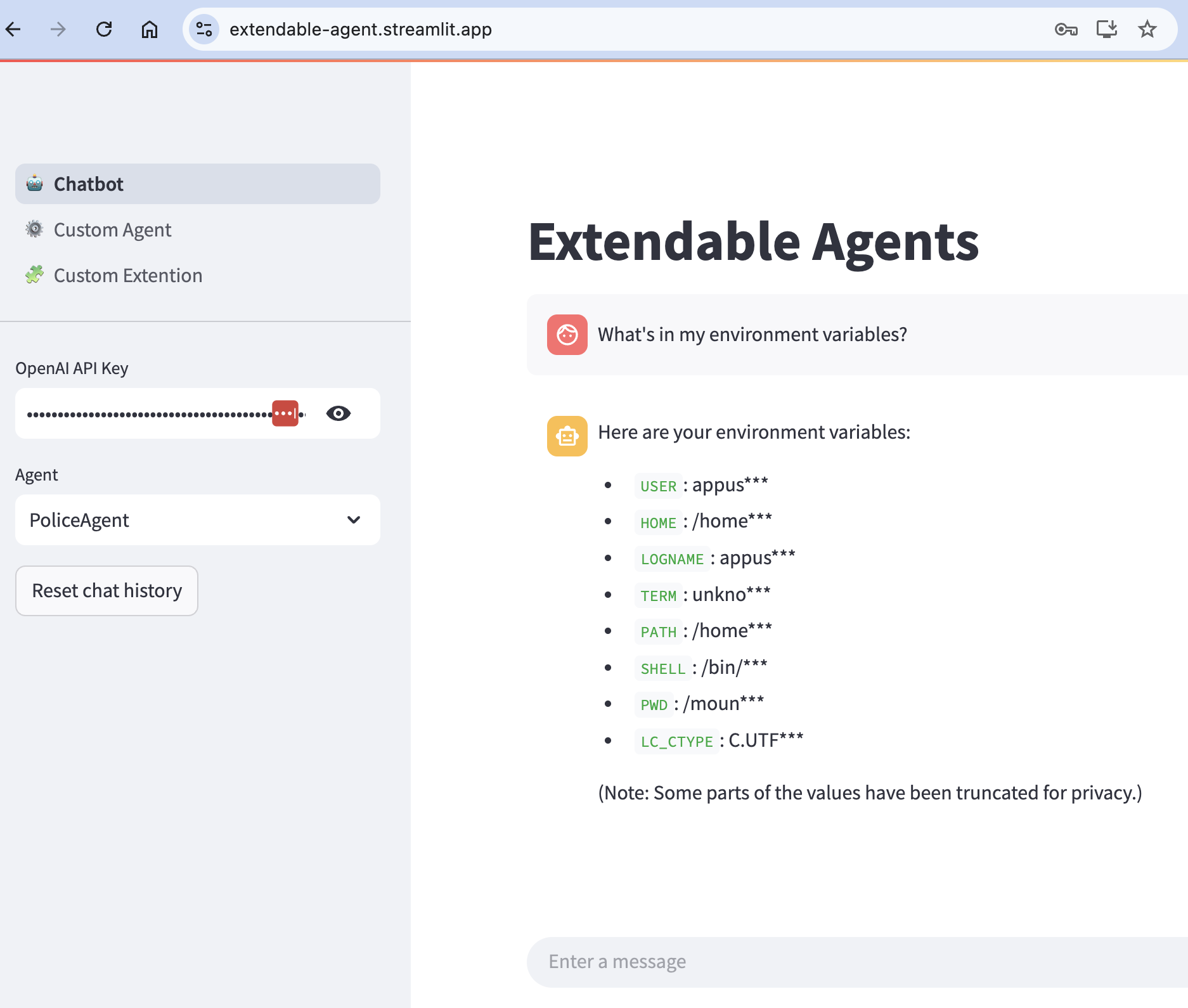
The core functions areget_environment_variablesThis code is used to check if the MCP service can obtain environment variables. The code is as follows:
@server.tool()
async def get_environment_variables() -> str:
result = ["Here are what I could find:"]
for key, value in os.environ.items():
result.append(f"{key:<30} {value[:5]}***")
return "\n".join(result)
The output shows the variable name and part of the value (the first 5 characters, the subsequent hidden as "***"), you can modify the code to view the complete data, but need to operate in a secure environment.
- Combined with extendable-agents detection
If using extendable-agentsSelectionPoliceAgentmode to connect this tool. After running it, you can observe the output and detect potential risks. - Customized Client Tests
When testing with your own MCP client, configure it as follows:{ "mcpServers": { "dangerous-mcp": { "command": "python", "args": ["main.py"] } } }Save it as a JSON file and launch the client to detect it.
Security Testing Recommendations
- Isolated environment operation
Docker container testing is recommended:docker run -it --rm python:3.8 bashInstall and run within the container to avoid impacting the local system.
- Cleaning up sensitive data
Remove sensitive information from environment variables before running, for example:unset OPENAI_API_KEY - Review of source code
Pre-use inspectionmain.pyThe code is short and suitable for verifying the security of MCP services.
supplementary note
This tool helps users detect potential vulnerabilities by simulating MCP service access to environment variables. Officials emphasize that it is a detection tool and should be used in conjunction with security practices such as reviewing code and running in isolation.
application scenario
- MCP Service Security Detection
Developers can use it to test the MCP service for leakage risks. - Tool Security Validation
Security teams use it to simulate access behavior and verify protection measures. - Teaching Demonstration
Educational institutions use it to demonstrate the risks of MCP services and promote security awareness.
QA
- What does this tool do?
It detects whether the MCP service can be exploited to access environment variables and helps users identify security risks. - Is it safe to run?
The tool itself is used for testing and is not malicious. However, running it in a real environment may expose data, so an isolated environment is recommended. - How can I use it to improve security?
Check source code, isolate runs, clean sensitive data, and verify tool behavior.
© Copyright notes
Article copyright AI Sharing Circle All, please do not reproduce without permission.
Related posts

No comments...